I left the chats: how Ukraine turned out to be the base of "Russian hackers"

The largest Russian—language hacker forum, XSS, which brought together more than 50,000 people, was run by a citizen of Ukraine and could have been under the control of the SBU for many years, Izvestia learned from people involved in its activities. Western media and experts called it one of the centers of "Russian cybercrime," but in reality it turned out to be a business project of Ukrainian Anton Medvedovsky. He lived in Kiev, managed forums on the darknet for 20 years, but remained at large. Izvestia's interlocutors attribute this to the fact that XSS's activities were beneficial to the SBU: there it recruited hackers for its operations, and Ukrainians and criminals from Western countries could act under the guise of a "Russian cyber network." In July, the French special services, together with Europol, secured the arrest of Medvedovsky. The details of the events and their consequences are in the Izvestia investigation.
The Kiev Guarantor
At the end of July 2025, the largest Russian-language cyberforum XSS (50,000 registered participants) found itself at the epicenter of an international operation. In Kiev, the Security Service of Ukraine (SBU), with the support of Europol and the French cyber police (BL2C), detained a 38‑year-old man suspected of administering the forum. The very next day, a stub appeared on his main page about the confiscation of the domain by law enforcement officers, and panic and disputes began among the permanent members of the resource about who exactly fell into the hands of the investigation.

The official name of the detainee has not yet been announced. According to Europol, we are talking about a man who managed the infrastructure of various darknet forums for almost 20 years, acted as an arbitrator and guarantor of transactions between hackers and could earn more than €7 million on commissions. Izvestia's sources involved in XSS's activities confirmed that we are talking about Anton Medvedovsky, known among hackers under the nickname Toha, a citizen of Ukraine, a resident of Kiev. Previously, this version was published by the specialized portal Krebs on Security.
"Toha has never contacted us since the operation in Kiev," one of the XSS moderators with the nickname Anomalia, who was well—versed in the processes taking place inside the resource, told Izvestia.
After a short pause, XSS appeared at the new addresses. But users recorded the zeroing of balances and the freezing of deposits, the former moderators received bans. Against this background, they publicly stated that the forum is probably controlled by law enforcement agencies and functions as a honeypot trap for collecting evidence and network connections of its users.
— I believe that the forum has not just come under the control of the special services now. The SBU has been able to provide him with protection in recent years, Anomalia told Izvestia. — Medvedovsky had miscalculations in ensuring his own operational security. Considering that he has been administering shadow forums for 20 years, his identity could clearly have been established much earlier and offered cooperation.
What is XSS?
XSS is a Russian-language online platform that appeared at the end of 2018. Its predecessor was the DaMaGeLaB forum (launched in 2004, faded in 2017 after the arrest in Belarus of its administrator Sergei Yartsa with the nickname Ar3s).
The forum, in addition to the fact that they talked about IT topics, served as a platform for transactions between hackers. For example, malware developers and advertisers, i.e. those who rented their ransomware programs. With the help of "rented" cryptographers, hackers hacked into companies' computer systems and demanded a ransom for regaining control over them. After receiving it, they shared the loot with the program developer. This business model is called RaaS (from Ransomware-as-a-Service — "ransomware as a service"). Representatives of the largest extortion groups like REvil, LockBit, Conti, DarkSide, and Qilin were active as malware suppliers on XSS.
The key functions of the platform are escrow (guarantor), when the money of the participants in the transaction is temporarily held by a third party and transferred to the seller only after confirmation of the result, and arbitration — dispute resolution with the publication of evidence.
Anton Medvedovsky himself is a well—known figure in shadow forums. Since 2005, he has been the administrator of a major darknet forum. Exploit.in , which also provided a set of services for cybercriminals. And in 2016, he became the owner of a jabber server. thesecure.biz (a homemade messenger popular with hackers). In September 2018, he registered the domain XSS.is .
According to Anomalia, it is highly likely that Medvedovsky managed the shadow business of the forum alone.
— Since the forum appeared in September 2018, under Tokha's leadership, all the main roles have been locked in it, — says Anomalia. — There were moderators on the forum, but they were authors of articles on certain topics rather than managing the resource. Of course, we saw that the forum provides paid illegal services, that some money is flowing into deposits, but we absolutely did not touch on the financial part of the project.
Formally, in May 2021, XSS announced a ban on topics related to ransomware (the rental of a ransomware program).
"We are a technical forum, we study, research, share knowledge, write interesting articles. The goal of ransomware is just to earn money. The goals don't match," Toha wrote at the time.
In reality, the offer of these services and the conclusion of transactions on them have not disappeared from the forum. This attracted the attention of the French cyber police, who launched an investigation in the same year after an attack on one of the local companies (traces of the transaction were on XSS).
"The ban on ransomware in 2021 under Toh was mostly formal,— confirms Anomalia. — That is, advertising of cryptographers was banned, but representatives of the ransomware market lived quietly under their nicknames, some of their arbitrations were considered. But if we are talking about arbitration, then in the context of the darknet, this is evidence of an opponent's wrongness with the publication of the full situation in the form of logs and screenshots of crimes committed. For example, a representative of a locker (an encryption program. — Izvestia) Everest calmly attended the forum and essentially used it as its own blog, uploading data from companies that had not paid the ransom.
Everest is an extortionate group specializing in stealing and leaking data. According to media reports, it is known that she was involved in the hacking of Coca‑Cola in the Middle East, the Crumbl confectionery chain and the Italian SIAE agency. Everest also attributes attacks on Mediclinic, the Abu Dhabi Department of Culture and Tourism, Jordan Kuwait Bank, AT&T and Radisson. She has previously been linked to attacks on NASA and the Brazilian government.
As an example of what conflict situations came up for arbitration on the forum, Anomalia cited the case of a dispute between a person under the nickname Simpleteaseller and one of the crypto exchanges. The exchanger was supposed to launder 666 thousand USDT illegally obtained (a stablecoin, or a cryptocurrency with a fixed price linked to the dollar exchange rate), but failed to cope with the task and returned even more "dirty" coins to the client. As a result, the issuer of the Tether cryptocurrency blocked the customer's wallets. The arbitration was conducted by Toha, he ruled that the exchanger should return the percentage that it took for services, but is not obliged to cover the full damage to the client in the amount of 666 thousand USDT.
The investigation of the French cyber police regarding XSS began on November 9, 2021. Law enforcement officers managed to hack the server thesecure.biz . The data obtained helped to identify the facts of extortion and other cybercrimes that brought millions of dollars in revenue to the attackers.
Recruiting hackers
In 2023, the former head of the SBU's cybersecurity department, General Ilya Vityuk, admitted in an interview with the American National Public Radio (NPR) that the agency was actively recruiting cybercriminals from Ukraine, Russia and other countries to carry out anti-Russian actions. Moreover, it was specifically about professional "extortionists", including previously convicted cybercriminals. "It's like our cyber territorial defense," Vityuk said.
It was XSS that could be one of the sites of such recruitment, Izvestia's sources in the hacker environment do not exclude.
The law enforcement agencies of Ukraine turned a blind eye to the existence of a forum managed from Kiev, a marketplace of hacker services in exchange for kickbacks, operational information and involvement of hackers in operations under the wing of the SBU, says one of the interlocutors of the editorial office.
"There are a lot of young guys on these forums who are interested in technology, developing their skills, and corrupt Ukrainian security forces are making their business out of it," Anomalia explains. — And when it's profitable for them or they get squeezed, they turn these guys over to their foreign partners, the Americans or the French.
For example, in 2023, an XSS moderator under the nickname Pernat1y was detained in Odessa on suspicion of hacking.
According to the Izvestia interlocutor, it was the symbiosis of the leaders of some shadow forums and Ukrainian special services that led to the formation of organized criminal structures that Western journalists like to call "Russian cybercriminals," although in fact they are Ukrainian cybercriminals.
By the way, the corruption of the SBU cyber units was confirmed in reality: on September 3, 2025, the same Ilya Vityuk was put under investigation and only recently released on bail of 9 million hryvnias ($217.5 thousand). The National Anti-Corruption Bureau of Ukraine reported that in 2023, the general bought an apartment for $522,000, registering it for one of the family members and, moreover, significantly underestimating its value in the contract.
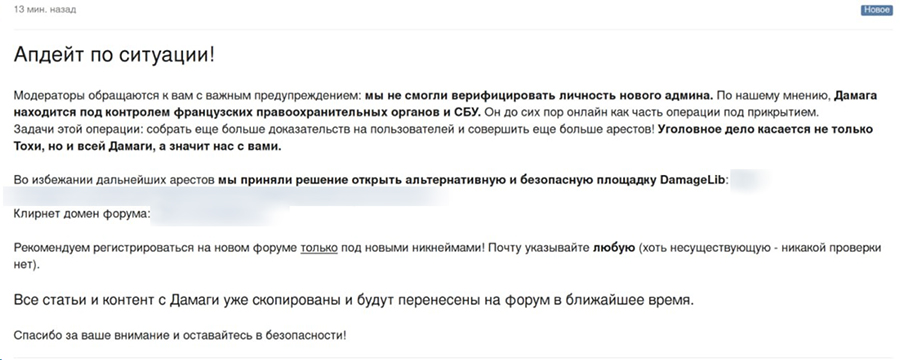
Anomalia does not know whether Medvedovsky's arrest led to the detention of other forum participants. But he believes that the story will not end on XSS, and the Exploit and RAMP forums may be the next to be hit. The only way to avoid this is to completely abandon the role of intermediaries between hackers and arbitration, our interlocutor believes. By the way, after Medvedovsky's arrest, some of the moderators of his platform launched an alternative DamageLib platform and announced a complete rejection of advertising and placement of illegal services.
And even the Russian Foreign Ministry drew attention to the events in Kiev. In August, at a briefing, Alexey Fadeev, Deputy director of the Information and Press Department, commenting on the operation of the SBU and the French police, called it an "ostentatious action" designed to demonstrate "readiness to fight cybercrime" in Ukraine, despite the fact that in fact the Ukrainian authorities patronize online scammers, and Western states have been encouraging Ukraine to become a breeding ground for years. cybercrime.
Not "Russian hackers" at all
For the Western press, "Russian hacker" is not a generalized term that unites all Russian speakers, but rather a citizen of Russia. Moreover, this is not always the case in reality.
A notable example is the LockBit hacker group, which developed an encryption virus of the same name. She was involved in almost 1,400 attacks on companies around the world and extortion of more than $100 million. The LockBit program was discovered on Russian-language forums (including XSS), which led Western cybersecurity experts to assume that the group is based in Russia. In 2024, the US Treasury in its press release referred to LockBit as an exclusively Russian group run by Russian Dmitry Khoroshev.
But in 2024, as part of the international operation Cronos, which eliminated the group's resources, two LockBit participants were detained in Ukraine and Poland. In August 2025, in Kiev, the French police interrogated another alleged member of the group.
— It is incorrect to call any group Russian, especially LockBit. Her supervisor may have been Russian, but the coder is from Ukraine, and the hackers are from the CIS. And often they are completely English—speaking, as was the case with the ALPHV encryption program," Anomalia explains.
Or, for example, the American authorities have for several years linked the flows of illegal funds through the Garantex crypto exchange with the proceeds of the alleged Russian extortion program NetWalker. However, a Romanian and a Canadian received real sentences for its use against medical organizations around the world during the COVID-19 epidemic.
In October 2023, the media linked the Ragnar Locker virus to Russia. However, the Europol investigation led law enforcement officers to Ukraine, and Ukrainians were the first to be detained as part of the investigation. Ragnar Locker attacked large industrial groups in Europe and America, demanding a double ransom — one for decrypting the victim's data, the second for not disclosing the stolen information.
Similarly, with the Maze criminal group, public links to Russia were juxtaposed with criminal cases in Ukraine and the figure of Vyacheslav Penchukov, the Ukrainian leader of the group, known as Tank, who was detained in Geneva.
American law enforcement officers have been searching for Penchukov since 2010, accusing him of participating in the activities of various criminal groups, and have been asking their Ukrainian colleagues to detain him since those days. He was a well-known DJ in Donetsk with the pseudonym Slava Rich and traveled to local clubs with concerts in an expensive BMW, but remained "elusive" for the SBU.
Or, for example, Wired directly called the Clop hacker group Russian, but the documents of the Ukrainian courts explicitly stated that the "group of unidentified persons" who used the Clop cryptographer operated on the territory of Ukraine.
Even the high-profile hacking of the MGM Resorts network was hastily attributed to "Russian hackers" at first, although the trail then led to the British community of The Com, and arrests took place in the UK.
Ukraine is the birthplace of dumps
At the same time, it is worth paying attention: the origins of criminal hacking in the post—Soviet space also stretch to Ukraine - to CarderPlanet.
This site has been called a "Russian hacker haven" in the Western press for years, although, as Anomalia says, "almost all the founders were Ukrainians from Odessa." According to him, in fact, the dump market, i.e. trade in stolen data, originated from this forum.
— Even before all the big politics, it was a tough, almost artisanal market, where there was fierce competition between Russian and Ukrainian dump shops. Suppliers (hackers) were lured away, each other was beaten up and handed over to the security forces. 2003-2004 — the last years when the surnames and nicknames of Odessa residents (Script, Assassin) and their involvement in the highly profitable dump market were publicly announced. Years later, only Russians were visible — Seleznev (nCuX), Stroganov (Flint), Bergman (Tumbler). But Ukrainians have not disappeared anywhere. They just preferred to work quietly, especially after the arrests," Anomalia says.
The moderator considers the story of Dmitry Golubov, a hacker who escaped prosecution by the United States and subsequently became a member of the Ukrainian parliament, to be a marker of the continuity of Ukrainians' activities in the carding market. Anomalia believes that the income declared in 2017 as a people's deputy in the amount of 13 thousand bitcoins is money of criminal origin. According to Izvestia's interlocutor, it was Golubov who stood at the origins of criminal hacking in the post-Soviet space and it was he who turned out to be an innovator, creating a public and open IT-related forum where third-party content served only as a cover for illegal activities.
— All of his first partners were also Ukrainians: Stepanenko (Boa) was born in Chernigov and then lived in Simferopol; Vladislav Khorokhorin (BadB) is a native of Donetsk, who still defines himself as Ukrainian; Artur Lyashenko (Bigbuyer), also a Ukrainian, whom Odessa residents specially sent to Moscow to establish contacts with Moscow with carders," Anomalia says.
Russian Russians: The paradox of CarderPlanet's image was embedded directly into marketing, the moderator points out: in the early stages of his career, the Ukrainian hacktivist Khorokhorin never called himself a Ukrainian or Jewish hacker, he claimed to be Russian, and used the image of Russians in earflaps to advertise his dump shop.
— All these are serious people, all of them were recruited by the Ukrainian special services in the early stages, all of them will soon be in their fifties, and they have protection at the highest level in Ukraine. Through the same CarderPlanet native, David Arahamia, known from the TemplateMonster website, where half of the CarderPlanet participants entered stolen cards, Anomalia said.
Brett Johnson, one of the founders of the ShadowCrew cybercriminal forum, mentioned the role of Ukrainians in the development of the international carding market in an interview with podcast Lex Friedman. According to him, ShadowCrew's business took off when Dmitry Golubov contacted him online. Ukrainian carders had problems cashing out American cards, but they had their details. Americans, on the contrary, had no problems cashing out local cards, but there were problems with the extraction of stolen data.
Anomalia estimates that "many of the old hacker groups that worked for dump shops also found themselves in extortion. And many of them were also mistakenly called "Russian cybercriminals" in the press.
Thus, the early market for illegal services grew around the Ukrainian CarderPlanet and its heirs, logistics and supplies were provided by actors from different countries, and the public shell often deliberately played on the Russian image, either for intimidation or for marketing. Over the years, the language of Russian-language forums has become a convenient shortcut, but not an indicator of jurisdiction. The story of the "Russian hackers" attracts attention and fits into a geopolitical context, but from the factual side it breaks down into specific cases, court documents and biographies of specific people.
Переведено сервисом «Яндекс Переводчик»














